How to Open TCP Remote Access to Docker
By default, docker daemon only listens for connections on a Unix socket. This means that only local clients can connect to the Docker daemon. However, it is possible to configure Docker to accept remote connections by setting it up to listen on an IP address and port as well as the Unix socket.
Configuring
Now, lets get started with setting up remote access. There are two ways to do that - with systemd and daemon.json file. I prefer systemd approach and will describe it here.
- Use the command
sudo systemctl edit docker.serviceto open an override file fordocker.servicein a text editor. - Add or modify the following lines, substituting your own values:
[Service]
ExecStart=
ExecStart=/usr/bin/dockerd -H fd:// -H tcp://127.0.0.1:2375
Pay extreme attention to the comments in this file, as it tells you exactly where to put those lines:
### Editing /etc/systemd/system/docker.service.d/override.conf
### Anything between here and the comment below will become the new contents of the file
[Service]
ExecStart=
ExecStart=/usr/bin/dockerd -H fd:// -H tcp://192.168.1.85:2375
### Lines below this comment will be discarded
### /lib/systemd/system/docker.service
Note that I’m putting my host’s IP address rather than 127.0.0.1, because otherwise it won’t be visible from outside the local machine, which is why we are doing the exercise in the first place.
-
Save the file.
-
Reload the
systemctlconfiguration withsudo systemctl daemon-reload. -
Restart Docker with
sudo systemctl restart docker.service. -
Verify that the change has gone through by running
sudo netstat -lntp | grep dockerd. You should see output similar to this:
sudo netstat -lntp | grep dockerd
tcp 0 0 192.168.1.85:2375 0.0.0.0:* LISTEN 5568/dockerd
Off-topic
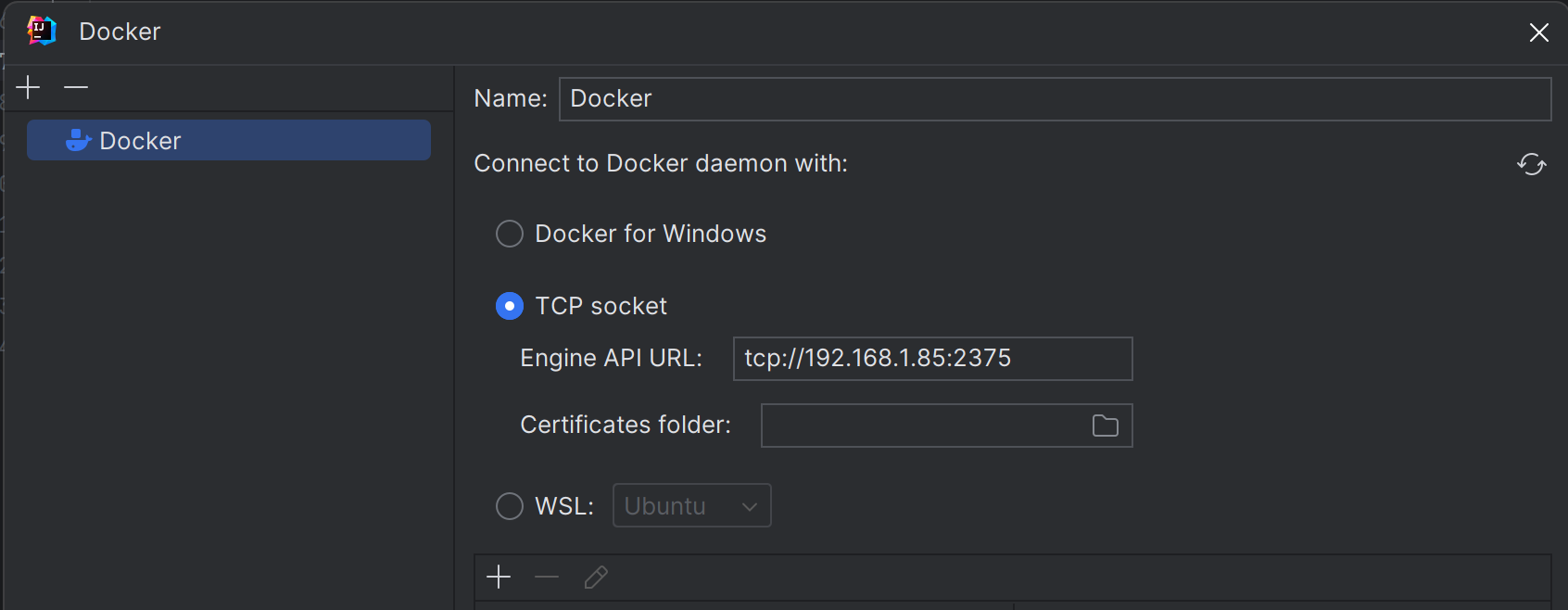
I can now even connect from IntelliJ IDEA:
Security Implications
Before we dive into the details of how to set up remote access, its important to note that there are security implications to opening Docker to the network. If steps aren’t taken to secure the connection, its possible for remote non-root users to gain root access on the host. For more information on how to use TLS certificates to secure this connection, check out Protect the Docker daemon socket.
If you are running docker daemon with -H tcp://0.0.0.0:XXX or similar you are exposing un-encrypted and unauthenticated direct access to the Docker daemon. If the host is internet connected this means the docker daemon on your computer can be used by anyone from the public internet.
Solutions
There are several solutions available for securing the TCP socket for Docker.
Using SSH
You can use SSH to protect the Docker daemon socket by creating a docker context to connect with a remote dockerd daemon using SSH. After creating the context, use docker context use to switch the docker CLI to use it, and to connect to the remote engine. Alternatively, you can use the DOCKER_HOST environment variable to temporarily switch the docker CLI to connect to the remote host using SSH.
Using TLS (HTTPS)
If you need Docker to be reachable through HTTP rather than SSH in a safe manner, you can enable TLS (HTTPS) by specifying the tlsverify flag and pointing Dockers tlscacert flag to a trusted CA certificate. In this way, you can configure TLS so that clients without a matching certificate will be blocked from accessing Dockers TCP socket.
To set up TLS, you need to create SSL certificates, then set up Docker Engine to require TLS connections. You can do this by creating a Certificate Authority (CA) for your TLS configuration, then generating server and client keys and certificates. Once you have created your certificates, you can configure Docker Engine and your clients to use them.
To contact me, send an email anytime or leave a comment below.
