How to give Azure Active Directory application access to manage your Directory

Recently I’ve ran into a task of creating a Web Application in Azure AD which in addition to usual authentication scenarios must also provide a custom management API for company admins to create users, roles, groups etc. This is where the journey with AD permissions started. I was able to create users, but not application roles. I couldn’t delete users as well etc. telling me I don’t have enough permissions to do certain operations.
This article describes how to grant required permissions to your Web Application so that it can do all that high privileged stuff. I’m assuming you have already created the app and configured your code to use application key and all the rest.
In essence there are two types of application permissions in AAD:
- Delegated permissions are used when accessing as a User, you need to authenticate as one of the users in this directory
- Application Permission is when you are calling as an application, which means you will need to authenticate with a secure key.
Permission Weirdness
If you have more than one directory in Azure portal, you need to login to PowerShell with a user in that directory specifically. The user can be created with usual means and assigning him a proper role:
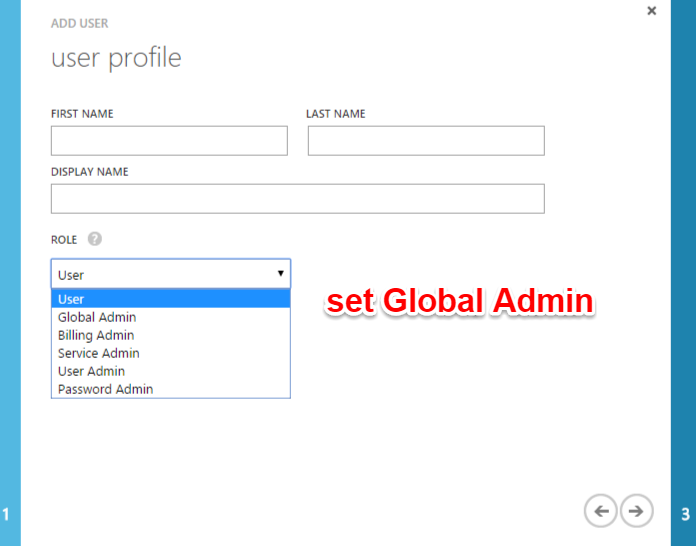
PowerShell Sequense
In order to connect to Azure you need to start the Windows Azure Active Directory Module for Windows PowerShell:
then type
Connect-MsolService
where you will be presented with login dialog
![Image [2]](image-2.png)
You have to enter credentials of the user which belongs to your particular directory, otherwise PowerShell will only give you rights to manage the primary company directory which you may have no access to.
List all application principals
In order to find your application’s principal id run the following command:
Get-MsolServicePrincipal | ft DisplayName, AppPrincipalId -AutoSize
Application principal is basically a unique application ID. Every time you install an application in Azure it will get a unique key.
![Image [5]](image-5.png)
You will see your application in the list, note the ID.
Find app principal ID
Now that application is found in the list you need to get application’s service principal ID. Service Principal is another Azure object which links an application with your tenant. In multi-tenant scenario each tenant using your application will have it’s own Service Principal. Now getting the Service Principal ID:
$webApp = Get-MsolServicePrincipal –AppPrincipalId id-from-above
![Image [6]](image-6.png)
Object Id in this screenshot is the Service Principal Id.
Grant the “Company Administrator” permission
In order to perform “dangerous” operation you need to assign Company Administrator permission to the application to your tenant’s Service Principal:
Add-MsolRoleMember -RoleName "Company Administrator" -RoleMemberType ServicePrincipal -RoleMemberObjectId $webApp.ObjectId
![Image [3]](image-3.png)
Once this is done your code must be able to do all sorts of funny stuff without any restrictions!
To contact me, send an email anytime or leave a comment below.
